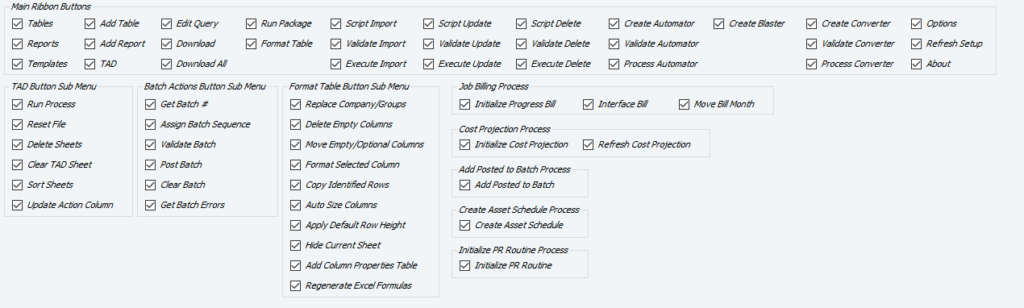
Getting Started #
TAD has five aspects of security, and all but one are driven by the Vista access of the user:
- Table Security – Driven by Vista Form security.
- Report Security – Driven by Vista Report security.
- Attachment Security – Driven by Vista Attachment security.
- Data Security – Driven by Vista Data security.
- Ribbon Button Security – Driven by the TAD Licenses form.
Table Security #
Table Security allows you to control the following actions for each table:
- Allow Download
- Allow Import
- Allow Update
- Allow Delete
Every TAD Table is linked to a Vista Form. If the user has access to the form in Vista, they will have access to the linked table in TAD.
Most TAD Tables have a corresponding Vista form, referred to as Primary Matches. Others, like the posted transaction tables (e.g., JCCD – JC Cost Detail), do not have an exact match, and these are referred to as Secondary Matches.
When reviewing VA Form Security in Vista, the following applies to how security is generated:
- Primary Matches
- If Access is 0-Full, the user will have Allow Download checked.
- If Add is checked, the user will have Allow Import checked.
- If Update is checked, the user will have Allow Update checked.
- If Delete is checked, the user will have Allow Delete checked.
- Secondary Matches
- If Access is 0-Full, the user will have Allow Download checked.
- The Add, Update, and Delete checkboxes will not affect the Allow Import, Allow Update, or Allow Delete checkboxes.
This structure ensures that security access in TAD is tightly integrated with Vista’s form and table security settings. Let me know if you’d like any adjustments!
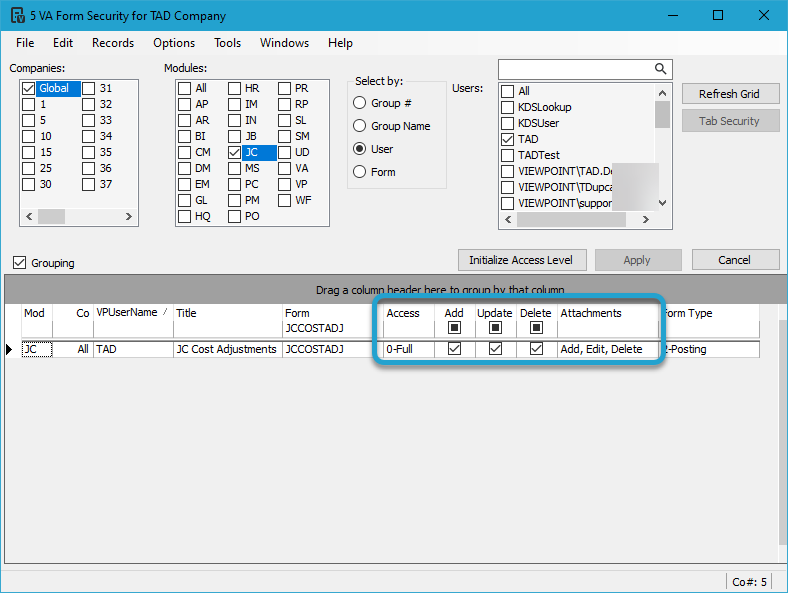
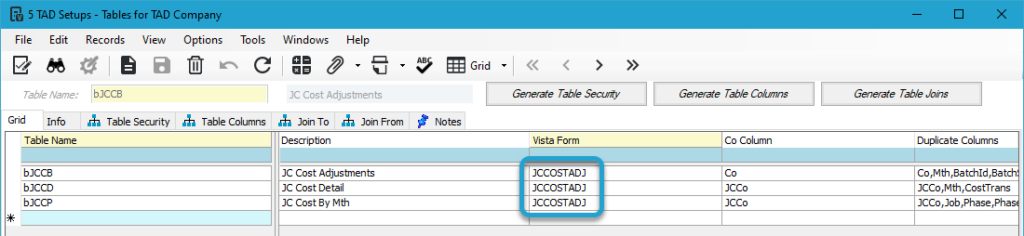
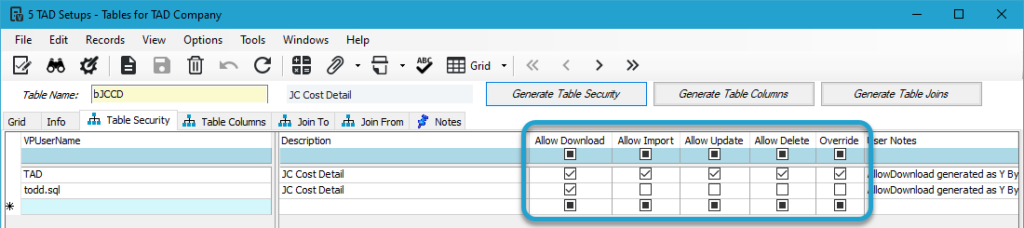
The image below shows multiple tables linked to the JCCOSTADJ (JC Cost Adjustments) Vista Form.
The bJCCB table is the Primary Match for JC Cost Adjustments, so all Allow checkboxes are checked.
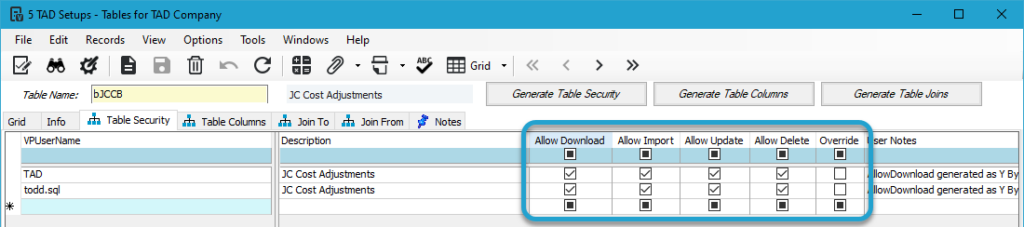
The bJCCD table is the Secondary Match for JC Cost Adjustments, so only the Allow Download checkbox is checked.
You’ll notice that the first row has all checkboxes checked, including the Override box. This indicates that someone has overridden the default security settings that were generated.
Report Security #
Report Security allows you to control the following actions for each report:
- Allow Download
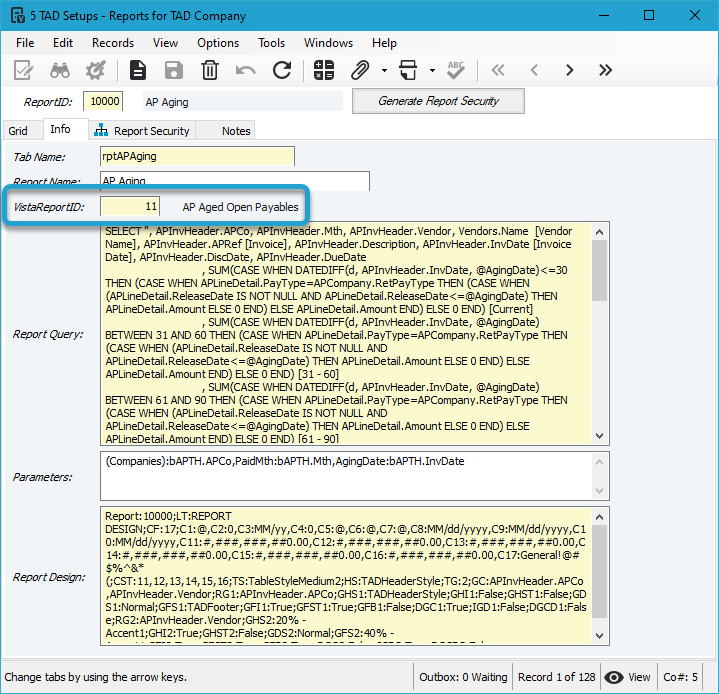
Every TAD Report is linked to a Vista Report. If the user has access to the report in Vista, they will have access to the linked report in TAD.
Most TAD Reports were created to replicate the same data as existing Vista reports, making them an easy match. For reports originating from TAD, a corresponding Vista report that produces the same data was chosen.
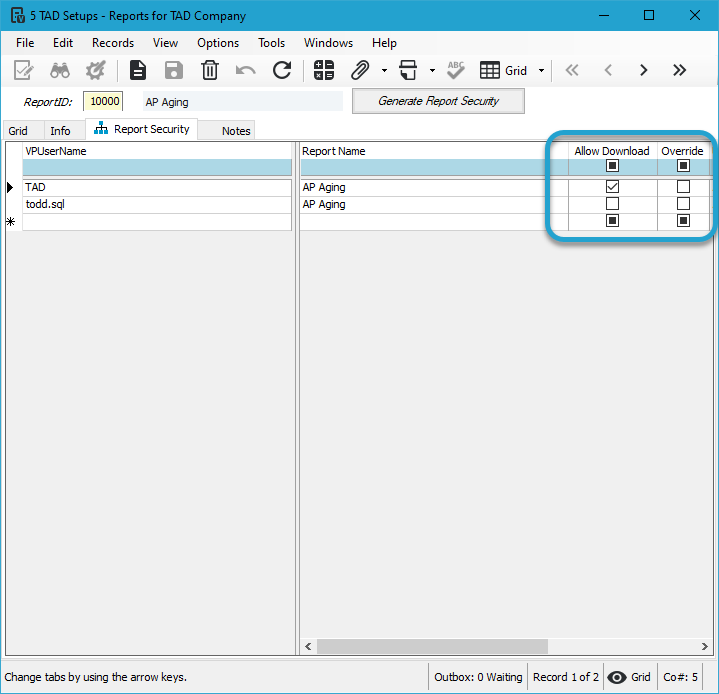
In the example below, the todd.sql account does not have access to AP reports, so the Allow Download option is generated as No. The Override box could be checked to grant that user access to the report.
Attachment Security #
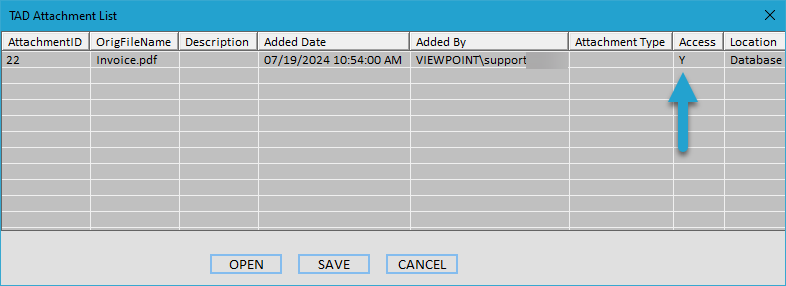
When a user opens the TAD Attachment List form, it will always display the attachment record(s), as shown in the screenshot below.
If the Access column shows a Y, the user will be able to Open or Save the attachment. If the Access column shows anything other than Y, the user will not be able to perform either action.
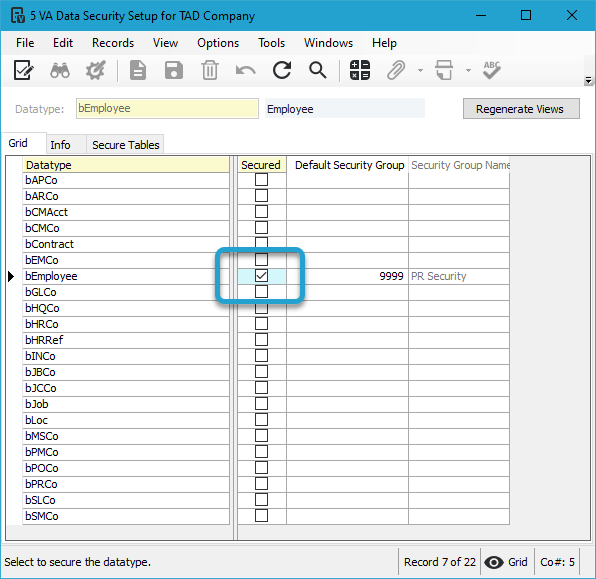
Data Security #
Although they are referred to as Tables, most users are actually using Views. Views are a layer on top of Tables where security can be applied. All secured datatypes in the VA Data Security Setup are still effective when users are downloading data using TAD.
If you’re using SQL Accounts to access TAD, make sure to assign the appropriate data security groups to the SQL Accounts in the VA User Profile in Vista.
Ribbon Button Security #
You control which buttons a user can click on the TAD Ribbon. Simply uncheck any button you don’t want the user to access, and they will receive an error message if they attempt to click it.
If a user has an Excel workbook open, the changes will not take effect until they close and reopen Excel.